Data view modes available in Staffcop Enterprise¶
Quite often we need to understand the way a certain file went including the users and protocols.
Or what side accounts a user has and if he sent any data from these accounts.
Relation graph is the best way to visualize this type of data.
In this view mode we can set a starting point to be some event and choose additional events to be the second and the third level of information detailing.
It’s reasonable to use three and more detailing levels for the required information.
It’s better to apply additional filters to the initial data.
Let’s take an example of creating an informative graph with the usage of all these advantages.
For example we learned that a sensitive file was accessed and we want to see the distribution of the file among users’ workstations.
We can narrow the initial data with the “file name” criterion that can be found in the dimension panel “File -> File name”, in this case the file is named «Миграция.docx» and there were 5 events related to this file.
To get the full picture we should analyze the events related to this file name or visualize the data to get more detailed picture.
For this we choose the “Analysis” view mode, then in the dimension menu we choose “File -> File name” then additionaly we choose the dimension “Data - Minutes” and finally the details for displaying “Senders” and “Recipients” in the “Messaging” dimension.
The output will be similar to this:
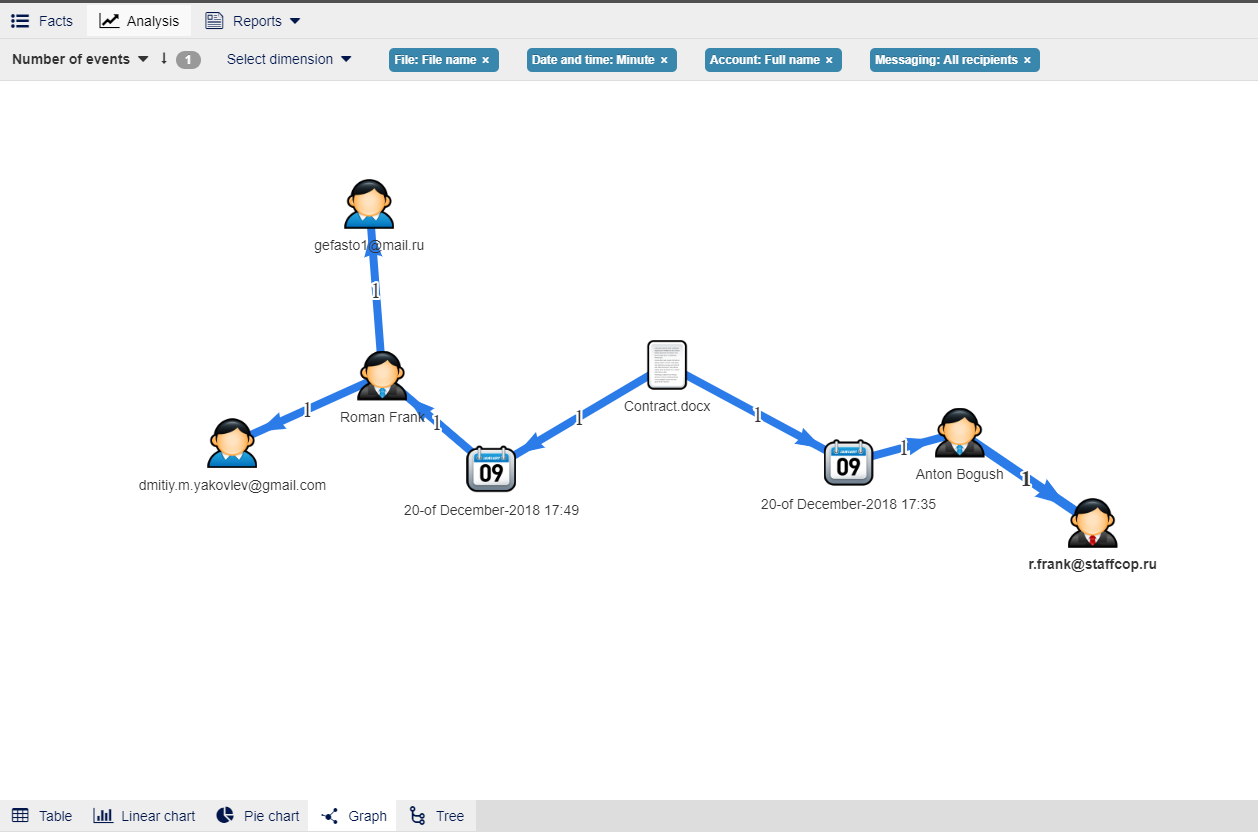
How can this picture be intercepted?
First, in the center of graph there is a file with it’s name that was previously found in the preliminary analysis of intercepted files.
We see the chain of dates of file transferring through various protocols. The first date when events related to this file appeared was 11.09.2017, when this file was sent in Skype from « live:zigzag18_1» to «live:at_1174».
Then at 20:42 this file was transferred from «ph.vochmincev@staffcop.ru» to «at@staffcop.ru».
The next event was at 20:44 when the user «at@staffcop.ru» sent an e-mail to «vs@staffcop.ru» with the file «Миграция» attached.
After that «vs@staffcop.ru» sent an e-mail to «da@staffcop.ru».
All these events can be quite legitimate but they vividly demonstrate the abilities of visualizing the distribution of files within the company, as we can see who receivedcreated the initial file and if he (she) then transferred the file to colleagues or outside the local network and the events happened to the file in meanwhile.