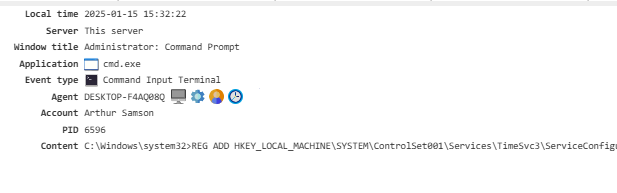
Event Types¶
All types of intercepted events are listed in Constructor. You can find them in the second column:
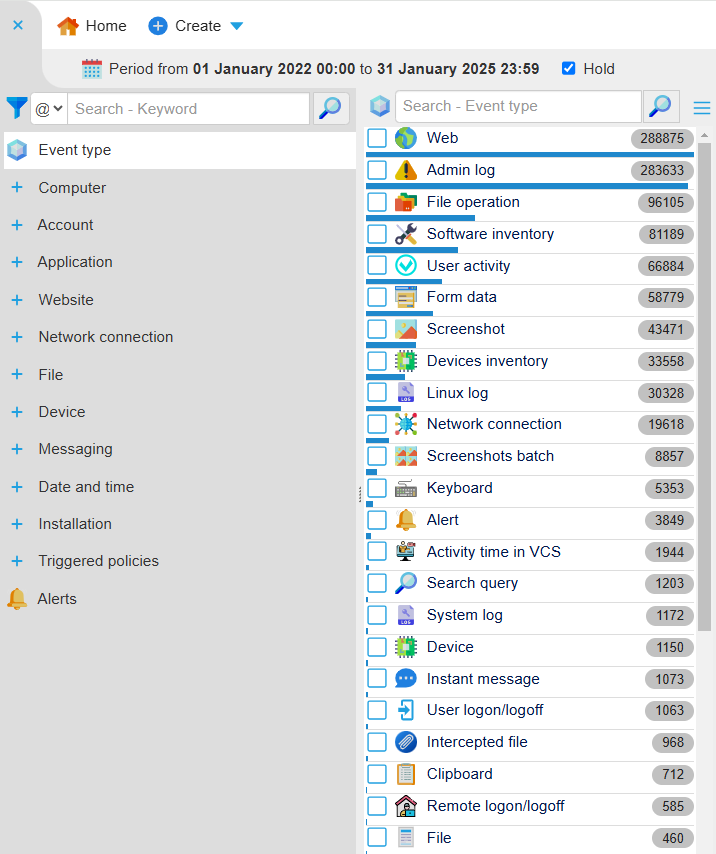
File Operation¶
Tracks file operations performed by applications like file managers, browsers, and other software.
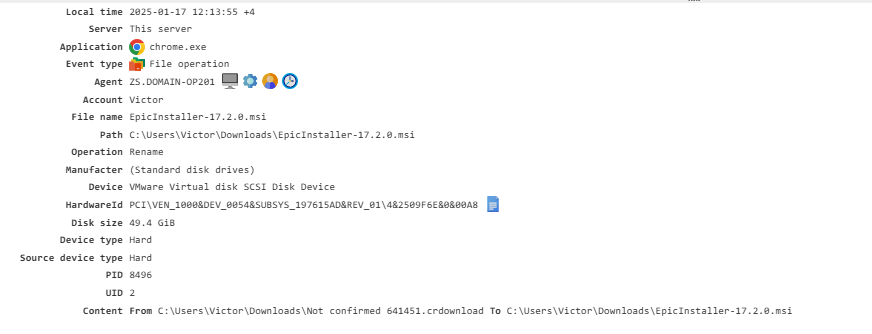
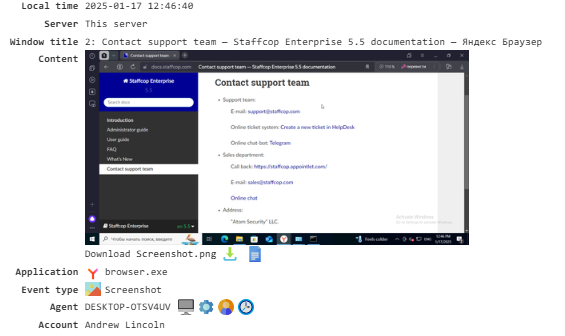
Screenshot¶
Captures screenshots of the user’s screen. You can adjust the frequency and quality of these screenshots in the Configuration section.
User Activity¶
Monitors the user’s activity time in applications and websites. This data is commonly used in reports. To enable this feature, turn on the**User Activity** module.
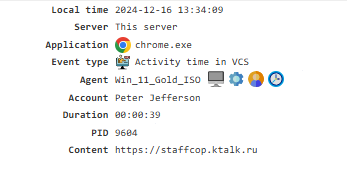
Activity Time in VCS¶
Tracks the amount of time the user spends in video conferences. To enable this event, the Video Conferencing Control module must be activated.
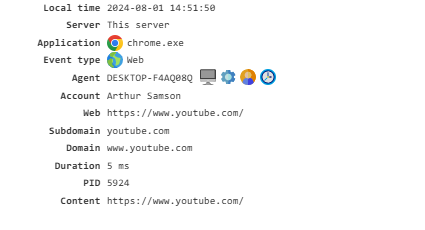
Web¶
Monitors the websites visited by employees. To enable this event, activate the Web Traffic and Network Monitoring modules.
Keyboard¶
Records keystrokes and key combinations in various applications, including intercepted passwords during Windows login. To enable this feature, the Keyboard Input and Low-level Keylogger modules must be activated.

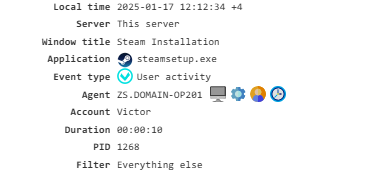
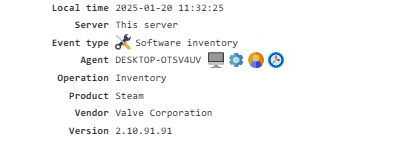
Software Inventory¶
Contains information about the software installed on the PC, collected when the configuration is updated and the agent is restarted.
To enable this feature, activate the Software Inventory module. The collected data is used in the Inventory-Software report.
Instant Message¶
Monitors instant messaging applications like Skype, ICQ, and others. To enable this feature, activate the Instant Messengers and Network Monitoring modules.
Mail¶
Tracks email correspondence.
Depending on the type of email you want to monitor, you need to enable the E-mail, Web Mail, and E-mail (MAPI/Exchange) modules. The Network Monitoring module must also be enabled.
Desktop Video¶
The Play button allows you to view all activities of the selected employee over a specified period of time.
To enable this feature, set up Screenshots and Desktop Video Recording in the agents configuration.
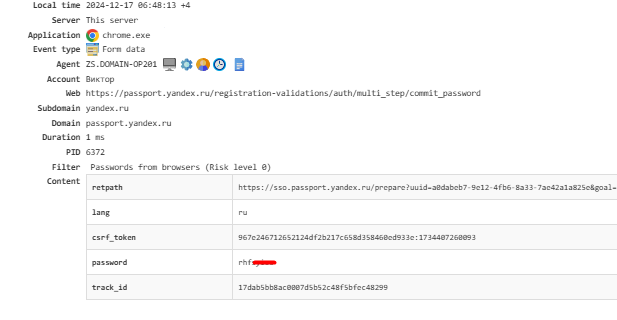
Form Data¶
Displays intercepted form data from internet browsers, including passwords entered in the browser. Captured passwords can be viewed under Triggered Policies → Passwords from Browsers.
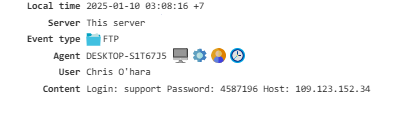
FTP¶
Displays details about all connections made to FTP servers:
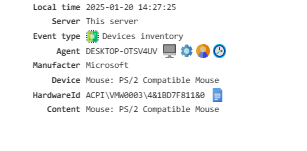
Devices Inventory¶
Provides a list of all computer devices with their IDs:
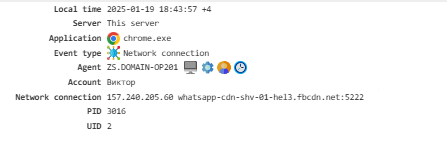
Network Connection¶
Tracks the IP addresses and ports used for connections. To enable this feature, activatethe Network Monitoring module.
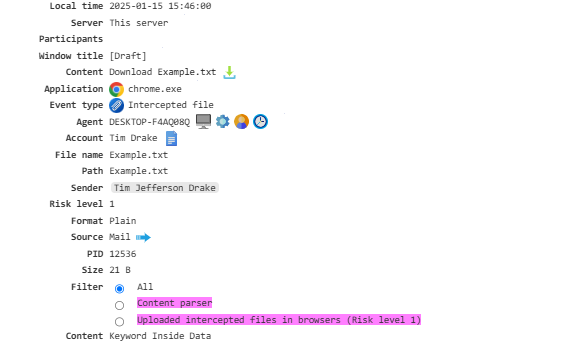
Intercepted File¶
Grants access to shadow copies of files sent via email, instant messengers, downloaded through browsers, file storage, and more.
To enable this feature, the Shadow Copying and File System Activity modules must be enabled.
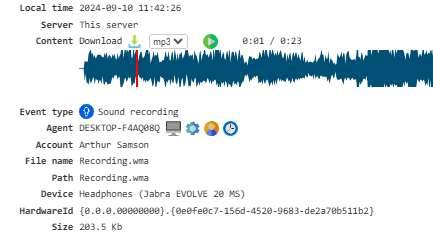
Sound Recording¶
Enables sound recording.
To use this feature, activate either Microphone Recording or Speaker Recording modules and configure your microphone recording settings. A microphone is required for recording.
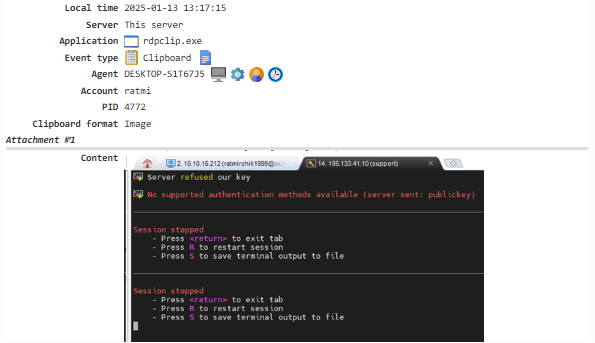
Clipboard¶
Captures both text and images copied to the clipboard. To enable this feature, activate the Clipboard module.
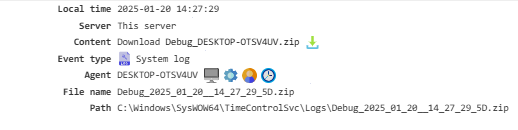
System Log¶
This data is mainly used to troubleshoot issues with the agent or server. To access it, enable Debug Mode.
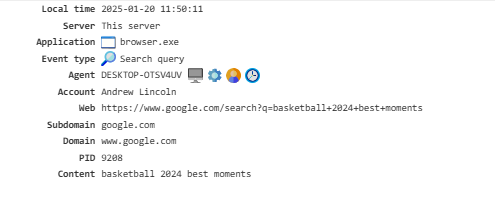
Search Query¶
Displays the queries entered by the user in popular search engines. To enable this feature, activate the Web Search Queries module.
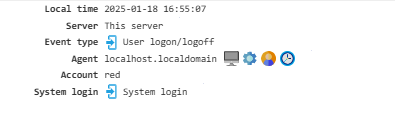
User Logon/Logoff¶
Shows details about user logins and logouts from the system.
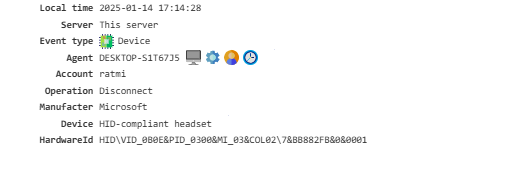
Device¶
Provides a list of devices connected to the PC.
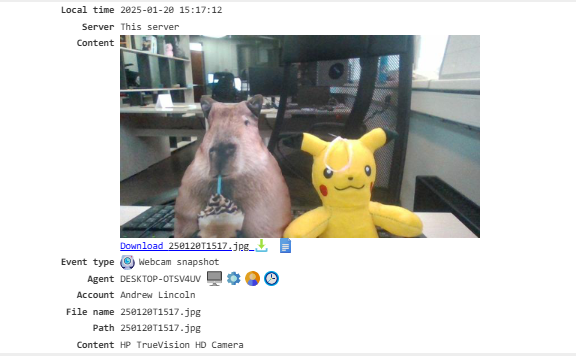
Webcam Snapshots¶
Captures snapshots from the webcam. To enable this feature, configure the webcam snapshot parameters and enable the Webcam Snapshots module.
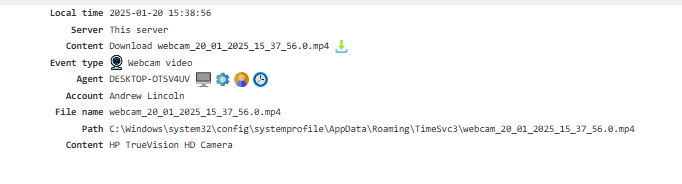
Webcam Video¶
Note
This feature was introduced in version 5.5 of Staffcop Enterprise. In earlier versions, videos are stored under the Webcam Snapshot event. If a new agent is used with an older server, video recording will not be performed.
Records video from the webcam in the workplace. To enable it, activate the Webcams module and switch on the Offline Webcam Recording option.
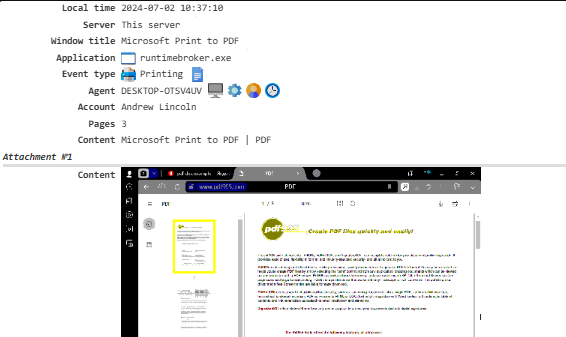
Printing¶
Tracks documents that are printed. To enable this feature, activate the Printing module.
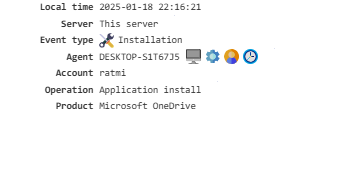
Installation¶
Provides a list of applications that users have installed on their PCs.
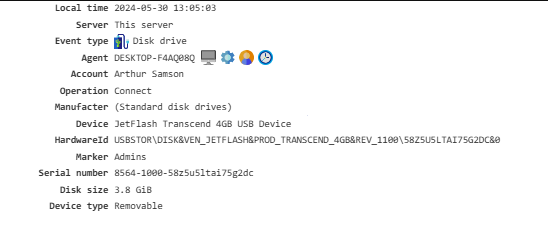
Disk Drive¶
Shows connected external storage devices.
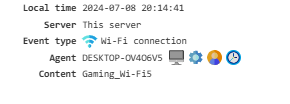
Wi-Fi Connection¶
Provides information about connections to wireless networks.
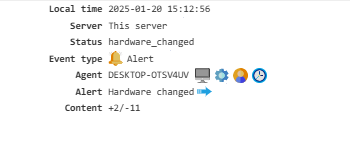
Alert¶
Displays event triggered by system policies.
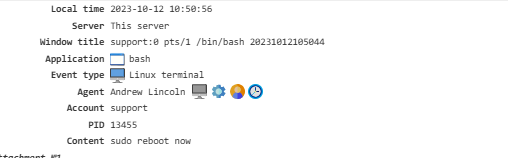
Linux Terminal¶
Captures data entered in the terminal, displayed as both text and a GIF file.
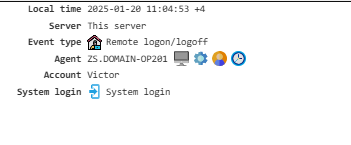
Remote Logon/Logoff¶
Details about remote logon and logoff activities using Remote Desktop (mstsc).
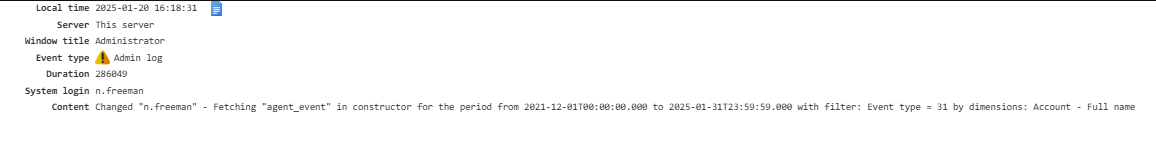
Admin Log¶
Logs all actions performed by administrators.
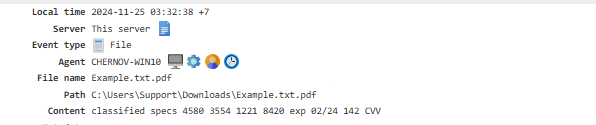
File¶
Shows the results of the file scanner’s activity.
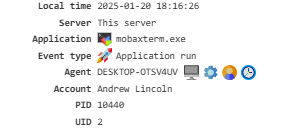
Application Run¶
Shows details about applications that have been launched.
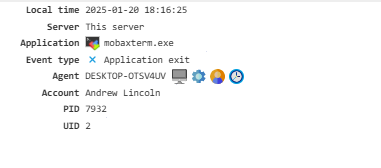
Application Exit¶
Shows information about applications that have been closed.
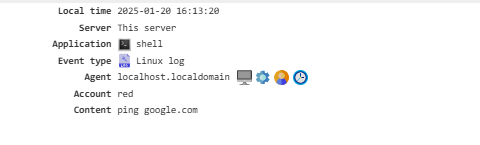
Linux Log¶
Records events from intercepted bash and other shell commands, along with syslog entries.
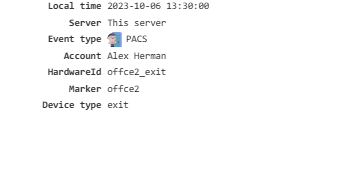
PACS¶
Logs events from the PACS (Physical Access Control System).
Command Input Terminal¶
Monitors commands entered in the CMD, recording both the command and its execution result. To enable this feature, activate Keyboard and Clipboard → Command Input Control in your configuration.