Data view modes¶
Often it is necessary to track a certain file, its source path, destination path, as well as intermediary nodes and transferring protocols
Or what accounts are used on a workstation and what information has been sent from these accounts
The best way to visualize this type of information is a relation graph.
In this view mode, you can use the value of an event as a starting point and select additional events as the second and third levels of information detailing.
When building graphs it makes sense to use the necessary information from three levels of communication.
Input data - it is better to apply additional filters on the input data.
Let’s try an example to realize the way you can use all these advantages and build an informative graph.
For example, we learned that access to a sensitive file was received, and we need to look at the distribution of the file in the network.
The input data can already be limited to the “File name” that can be found in the Dimension panel - “File - File Name”, in our case the file name was “Contract.docx”, we saw that the file had 2 events.
Then, to get a full picture you can analyze the events associated with this file name and visualize the received data.
Для этого выбираем в верхнем меню вид отображения - «Анализ» в меню измерений выбираем Фаил - «Имя файла», затем дополнительно выбираем измерение - «Дата - Минуты», и наконец детали для отображения «Отправителей» и «Получателей» в меню измерения «Переписка».
The output will be something like this:
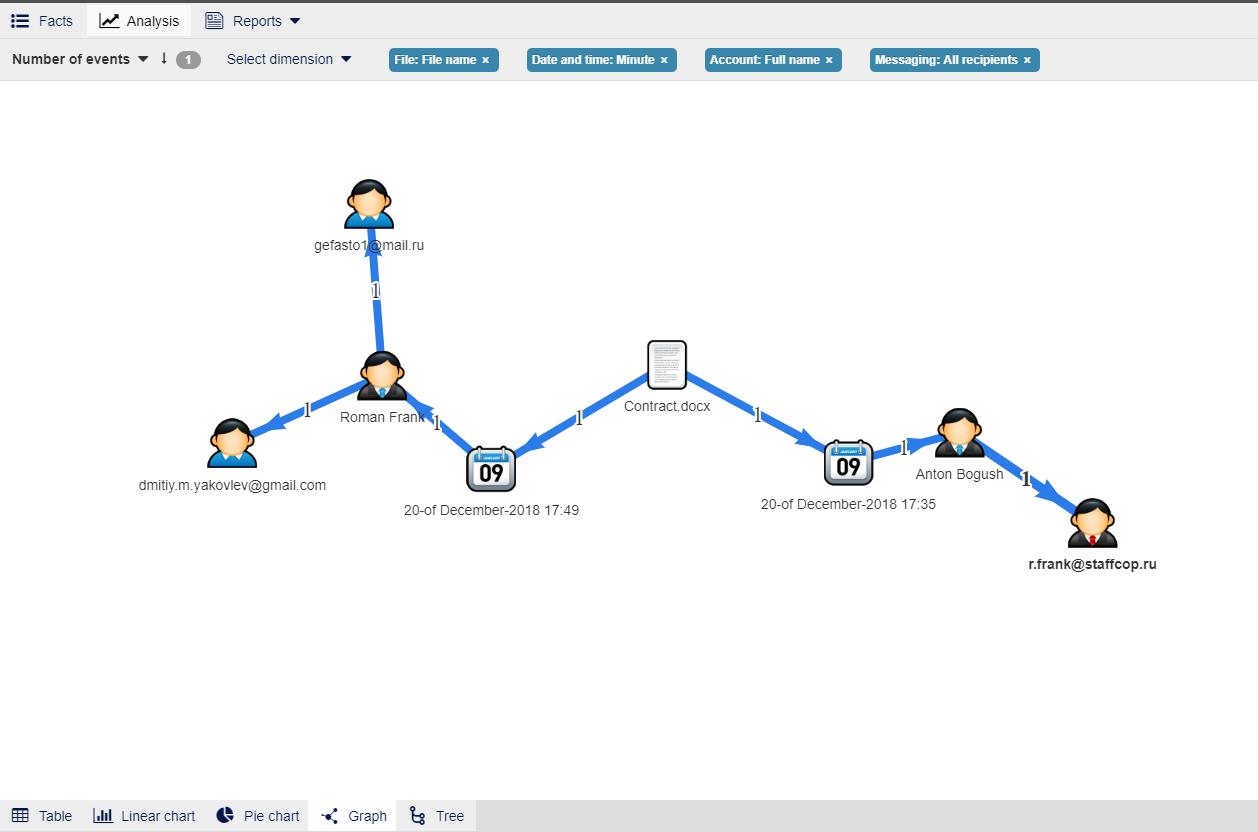
How can the results be interpreted?
First, in the center of the graph there is a file with the name we found earlier, from a preliminary analysis of intercepted files.
From it, the next in the chain are the dates of moving the file through various protocols. The first date of the event associated with this file is December 20, 2018 at 17.35, this is the event of sending the file from “Anton Bogush” to to the recipient “r.frank@staffcop.ru”.
Then the same file was sent in “17:49” by mail from Roman Frank to the recipient “gefasto1@mail.ru” and “dmitry.m.yakovlev@gmail.com”.
The account name Roman Frank seems to be connected with the e-mail of the first recipient - “r.frank@staffcop.ru”, most probably they represent a single person.
We can see that @staffcop.ru represent a corporate domain and the last two recipients of the file use public e-mails: mail.ru and gmail.com, which means that the file has left the corporate network.
These events could be quite legitimate, but they demonstrate the possibility of visualizing the movement of files inside the company and beyond, you can see who received the source file when it was transferred to colleagues or to the Internet and what else happened to this file after the file creation source no longer participated in the chain of transmission of it elsewhere.