Files¶
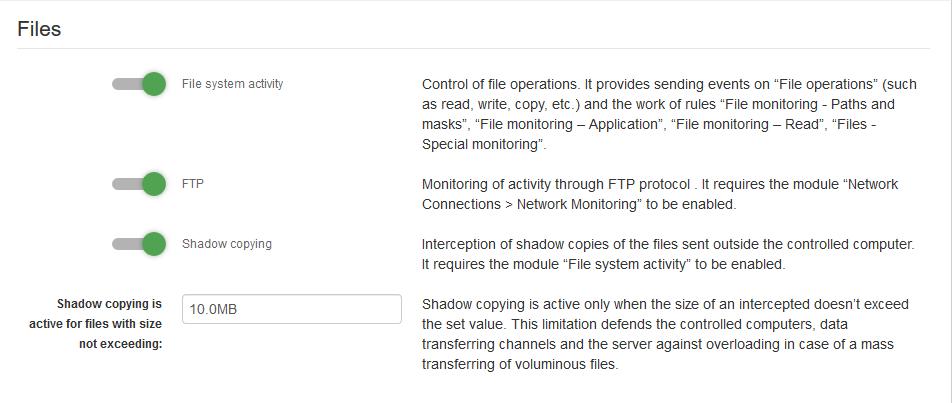
- File system activity - module for tracking file activity on a computer. Intercepts read, write, remove operations, etc.
Note
Incorrect configuration of this module can lead to performance drops on users’ workstations. If the task of monitoring file activity is not reasonable, disable this module to reduce the load.
- FTP - FTP connection monitoring module.
- Shadow copying is a module for intercepting shadow copies of files. Supports file interception of files:
- sent by e-mail (including using web-mail);
- sent to removable storage devices (USB drives);
- uploaded to the Internet via browsers (file sharing, cloud services, etc.);
- sent via instant messengers (QIP, Skype, ICQ, Mail.ru Agent, etc.);
- sent to print;
- interception of files sent in the browser to Google Drive.
- Shadow copy of files from removable devices - module for interception file listing from connected USB-drives and shadow copying of files if “Rules: Shadow copy of files from removable devices” is configured.
Rules: File monitoring - Paths and masks¶
Disallow - disables tracking file operations on the specified path or paths.
Allow - tracks file operations only for the paths specified in the list. All other file activity on any paths won’t be tracked.
Note
The following special characters are supported - «*» which means any number of characters before or after the stated line, «?» which means any single character of in this line.
Rules: File monitoring - Application¶
Disallow - disables tracking file operations by name of an executable file or a list of executable files. File operations of any other applications are tracked.
Allow - enables tracking file operations only for the stated executable file or a list of executable files. File operations of any other application are not tracked.
Rules: File monitoring - Read¶
Disallow - forbid tracking READ file operations for the specified list of executable files.
Allow - allow tracking READ file operations only for the stated list of executable files.
Rules: Files - Special monitoring¶
Allow - the specified list of files is copied at any action performed with the file. When reading/copying/access and other file operations a show copy of the file is created.
Note
Shadow copies of files will be recorded to corresponding operations in the event type “File” - “Operation” in the Constructor
Note
With intensive use, for example, of a directory title, a lot of shadow copies of files can be generated.
Rules: Shadow copy of files from removable devices¶
Allow - this rule contains masks for interception files from external devices.
Entries of the following format are supported
- *.docx - intercept of files with this extension.;
- name.* - intercept files by their names;
- *.* - intercept all files from the drive.
Warning
Be caruful with the rule *.*, it may lead to huge load on the server.