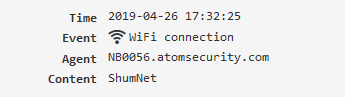
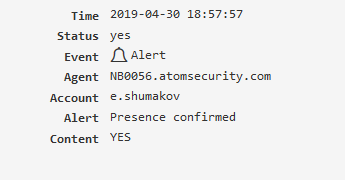
Event types¶
All types of intercepted events are listed in Constructor
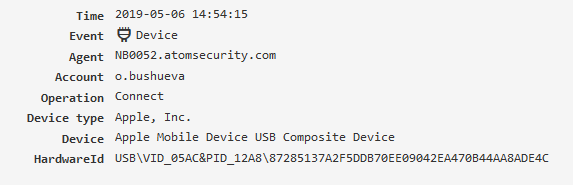
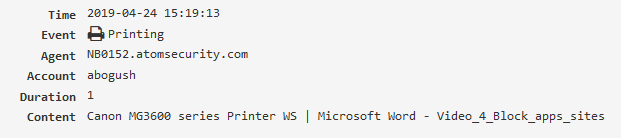
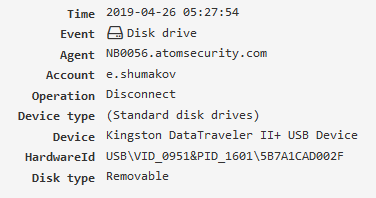
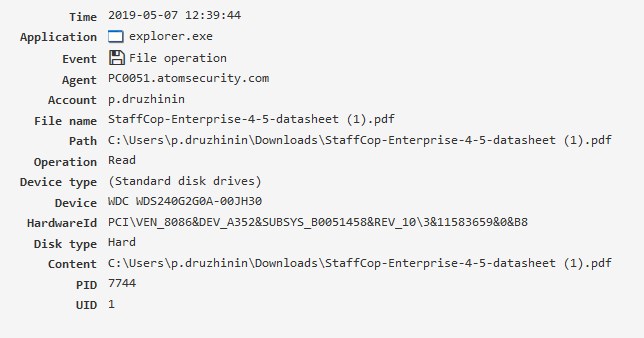
File operation¶
File operations performed by applications (file managers, browsers, other software).
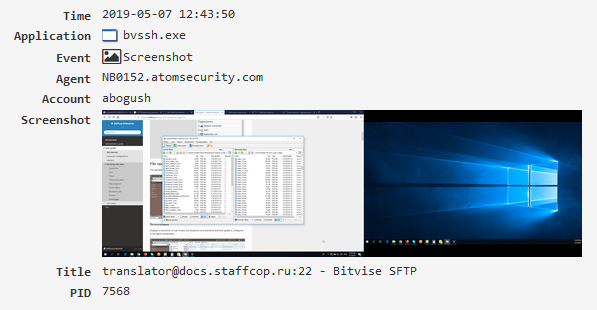
Screenshot¶
Displays screenshots of user screen, the frequency of screenshots and their quality is configured in the agent configuration.
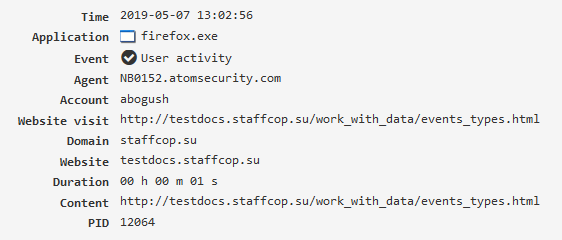
User activity¶
Contains the activity time of a user in applications and on web sites, it is used in reports. The “User’s activity” module must be enabled.
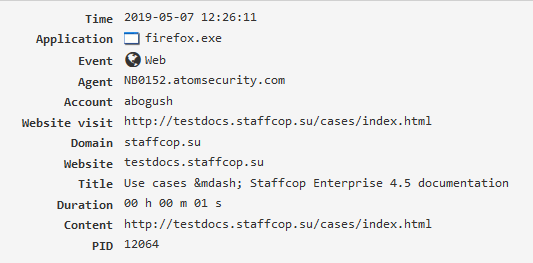
Web¶
Websites visited by an employee. The “Web traffic” and “Network monitoring” modules must be enabled.
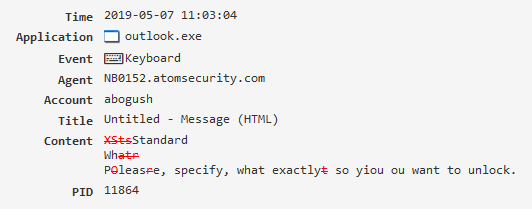
Keyboard¶
Displays keystrokes and their combinations in various applications, alsdisplays intercepted passwords when logging into Windows, the “Keyboard”“Low-level keylogger” modules must be enabled.
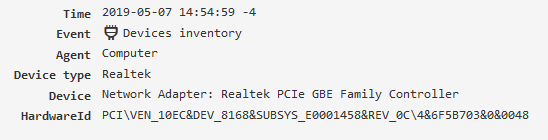
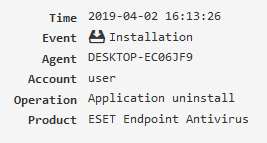
Software registry¶
It contains information on the software installed on the PC, it is collected when the configuration is updated and the agent is restarted.
It contains information on the software installed on the PC, it is collected when the configuration is updated and the agent is restarted.
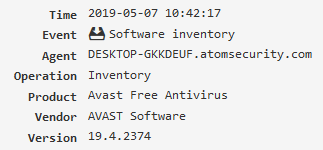
Instant message¶
Skype, ICQ, other messengers. For this to work, you need to enable the Instant messengers and Network monitoring modules.
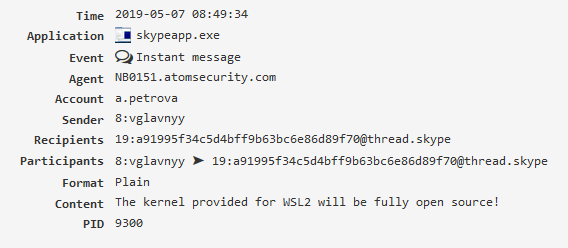
Mail¶
E-mail correspondence. For this to work it is necessary to enable modules “E-mail”, “Webmail”, “E-mail (MAPI/Exchange)” depending on what type of mail is of interest.
The “Network monitoring” module must be enabled.
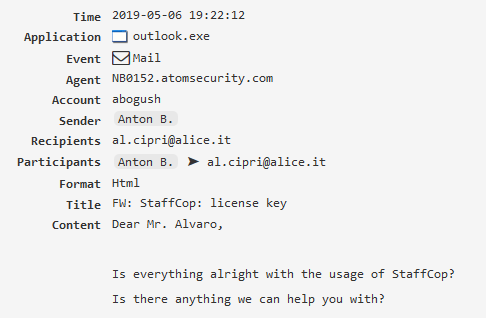
Desktop video¶
The “Play” button allows you to view all the activities of the specified employee for the desired period of time.
For this to work, you need to configure the “Screenshots” and “Desktop video” in the “Computer configuration”.
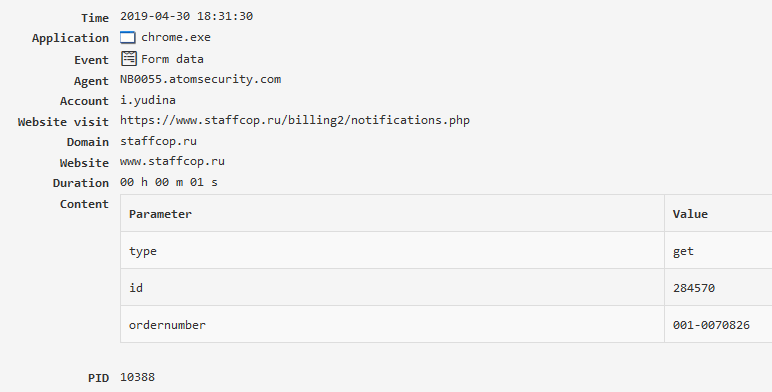
Form data¶
Displays details of intercepted web-forms from Internet browsers in the tabular form. It is used to intercept passwords entered in the browser, which can be viewed in the “Triggered filters” - “Interception of passwords in the browser”.
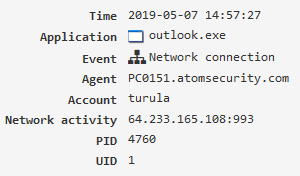
Network connection¶
Allows you to identify which IP addresses and ports were used for the connection. The “Network monitoring” module must be enabled.
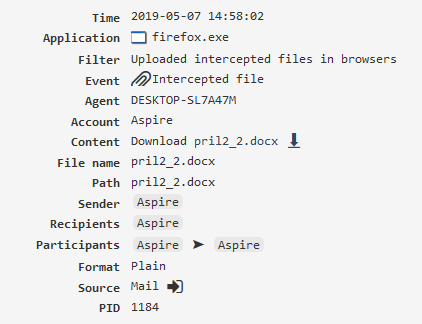
Intercepted file¶
You can access shadow copies of files sent by e-mail, Internet messengers, downloaded via browsers, file storage, etc.
The “Shadow copying” and “File system activity” modules must be enabled.
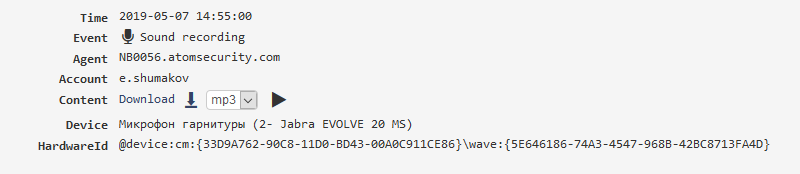
Sound recording¶
It’s possible to record sound from available microphones. For this to work, you need to enable the “Microphone recording” module and configure the recording parameters of the microphone.
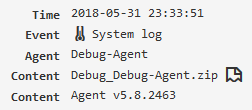
System log¶
This information is usually used to analyze the problems that have arisen with the agent or server. The “Debug Mode” must be enabled.
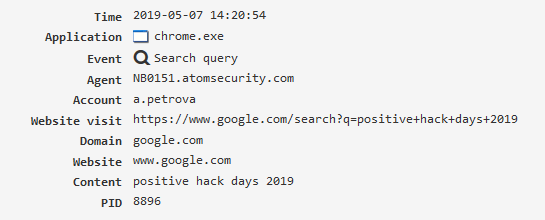
Search query¶
Displays the queries entered by the user in the popular search engines. The “Web search queries” module must be enabled.
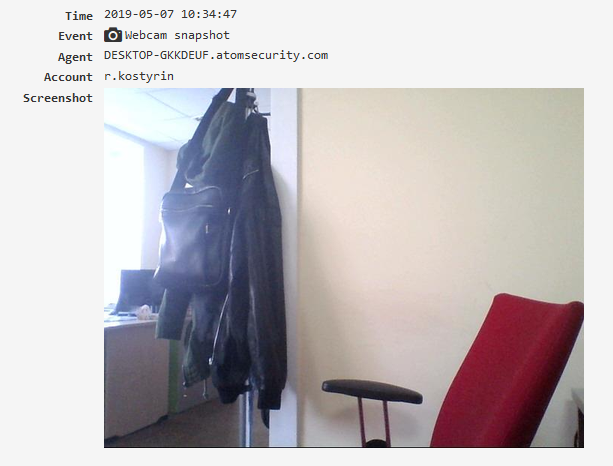
Web-cam snapshots¶
Web-cam snapshots. For this to work, you need to configure the settings of snapshots from the webcam and enable the “Webcam snapshots” module.